 |
| OBS Studio: My monkey enjoys the beach |
Monday, December 28, 2020
OBS on Linux: Green screen and virtual camera for video conferencing
Thursday, November 19, 2020
New Db2 V11.5 Mod Pack 5
During the currently ongoing virtual IDUG EMEA 2020 conference IBM released Mod Pack 5 for Db2 11.5. As it is with modification packs, it brings a long list of new features and enhancements to the current version of Db2. You can download this new release and other Db2 versions from the usual Db2 download page. As of this writing, the Db2 Docker image has not been updated.
Monday, November 16, 2020
Not just during Covid-19: Time for data masking
 |
| Facial data mask |
If you follow common sense or health agency / government instructions, you probably wear at least a basic face mask when mingling with other people. Mostly, this is to protect others from your droplets, possibly with some virus-laden payload. If the mask is more advanced, it is capably of filtering out stuff that may harm you.
Similar to face mask, data masks have been around for a long time. Data masks and face masks share the same purpose, preventing leakage of damaging "tiny bits". In the database system Db2, data masking is already built-in. You only need to apply data masking by defining masks (styling and sewing your own mask) and enabling them (putting it own). Here is how.
Wednesday, October 21, 2020
IBM Cloud: Considerations for role and resource setup
 |
| Solution architecture |
Monday, October 19, 2020
Terraform: Best practices for the cloud onboarding of enterprise projects
 |
| Architecture: End to end security |
When onboarding a new project — either on-prem or to a cloud environment — there should be no questions on how to get started. Onboarding should follow an enterprise-defined process based on (internal) standards. It needs to detail access roles and privileges and provide means to implement them.
Recently, in an IBM Cloud blog, I discussed such a project onboarding. Terraform scripts implement the rules as code — they help to automate roll-out and tear down access roles and privileges. The scenario from the solution tutorial "Apply end-to-end security to a cloud application" serves as specific example to proof-point the ideas.
Monday, October 12, 2020
Details available: IDUG EMEA 2020 as virtual conference
BTW: I recently participated in another virtual conference. The organizers sent out some goodies ahead of the conference, including yummy cookies.
Wednesday, September 30, 2020
Use alfaview on rpm-based Linux (Fedora, Red Hat, CentOs)
Recently, I tried to prepare for an alfaview session. alfaview is a video conferencing system and used by the university where I teach data security. Only earlier this year alfaview introduced Linux support, and only for Debian-based systems. My system is rpm-based (Red Hat Enterprise Linux / Fedora / CentOS), so what to do? A tool like alien did not work for me. Here is what I did to make alfaview run on my rpm-based Linux system.
Tuesday, September 15, 2020
Some fun digging into IBM Cloud access policies
On IBM Cloud, I have an account with multiple other users. To organize teamwork, I followed best practices for organizing users, teams, applications and made use of the IBM Cloud IAM (Identity and Access Management) capabilities.
With users, service IDs, access groups, and access policies in place, I wondered how to get insights into per-user privileges and the scope of service ID permissions. Sure, I could use the IBM Cloud console (UI) or the Command Line Interface (CLI), but why not test the API (Application Programming Interface) for some customized reporting? The script is available on GitHub.
Wednesday, August 26, 2020
Db2 and S3-compatible Cloud Object Storage
 |
| A look at Db2 and S3 storage |
Recently, I was contacted about an old blog post where I discussed how to access Cloud Object Storage from Db2. Since writing that article, both Db2 and (IBM) Cloud Object Storage have evolved. Thus, it is time for an update on how to backup data to cloud storage, load from external storage and even directly query data somewhere in the Internet...
Monday, August 24, 2020
IDUG EMEA 2020 goes virtual, moved to November 16-19
The recent meeting of the German Db2 User Group, DeDUG, was also a virtual event.
Update (2020-08-25): Seems the communicated dates were not final and I removed them for now.
Update (2020-08-26): Added information on IDUG EMEA 2021 and re-added November dates.
Monday, August 17, 2020
New JWT-based SSO in Db2 11.5
Wednesday, July 1, 2020
Db2 11.5 Mod Pack 4 is available
Wednesday, June 17, 2020
Getting started with Db2 on Cloud Lite
Wednesday, June 10, 2020
Hands-on security: Share resources on IBM Cloud
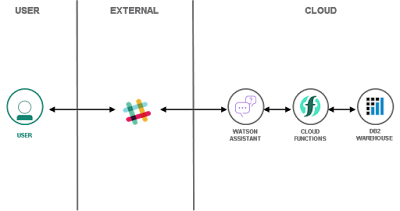 |
| Architecture: Database-driven Slackbot |
Tuesday, May 26, 2020
New performance and security feature in Db2: Authentication cache
 |
| New security feature in Db2 |
Wednesday, May 20, 2020
Use Chromium-based browsers to manage FIDO security keys
 |
| Add fingerprint to FIDO key |
Monday, May 18, 2020
Some advanced SQL to analyze COVID-19 data
 |
| Learn to write SQL |
Thursday, May 7, 2020
IBM Watson Studio: Download pandas DataFrame as CSV or Excel file
 |
| Gist code snippet |
From working with pandas DataFrames locally, I knew how to turn the data into CSV or Excel files. But working with a hosted environment, accessing the file system is not possible and some other solution is needed.
Monday, April 20, 2020
All the best combined: Cloud, Db2, Python, Serverless and Security
 |
| Add a cloud service ID as Db2 user |
All this helps to reduce the set of privileges held by a user or service and hence increases cloud security.
Tuesday, April 14, 2020
Home office and rubber duck debugging, 5 levels
 |
| Rubber duck debugging at home |
Wednesday, April 8, 2020
Key Protect as vault for multi-cloud setup
 |
| Guard credentials in a vault |
Tuesday, April 7, 2020
Encode credentials and upload to Key Protect
 |
| Protect credentials in Key Protect |
Wednesday, April 1, 2020
Covid19 phone challenge: My old Nokia has Android now
 |
| My reliable Nokia phone |
Tuesday, March 24, 2020
My best practices for 2FA and FIDO2 security keys
 |
| Some of my FIDO2 security keys |
Monday, March 23, 2020
Obtaining device metadata for FIDO / FIDO2 security devices
 |
| Zoo of FIDO2 security keys |
Wednesday, March 18, 2020
My best practices for home office - Corona edition
 |
| Take some rest |
Thursday, March 12, 2020
How to: Slack or email notifications for IBM Cloud security issues
 |
| Architecture for security notifications |
Tuesday, March 3, 2020
Use Cloud Functions for security scans (IBM Cloud Security Advisor)
 |
| Result of a serverless security scan |
Monday, March 2, 2020
Manage your Security Advisor custom findings from the command line
 |
| List Security Advisor notes via CLI |
Extend IBM Cloud Security Advisor with your own security metrics
 |
| Custom findings in Security Advisor |
Friday, February 28, 2020
Swashbooking for crowd-sourced book reviews and fun
 |
| Books for review |
Monday, January 27, 2020
25th meeting of German Db2 User Group
 |
| Celebrating the 25th DeDUG meeting |







