 |
| Architecture: End-to-end security |
FIDO2: An Overview
If you are not too deep into security, you might wonder, about FIDO2. FIDO2 is a joint project by the FIDO Alliance (Fast IDentity Online) and the W3C to provide strong authentication for web applications. Thus, it aims at more security by reducing or eliminating identity theft by providing password-less authentication. At the core of FIDO2 are cryptographic authenticators which can be hardware security keys connected via USB, NFC or built into, e.g., smartphones. The authenticators are combined with the WebAuthn protocol that defines how web applications, the computer (client) and authenticators interact. It is important to note that the authentication itself is performed by the cryptographic authenticator (the hardware). The computer (client) utilizes the Client to Authenticator Protocol (CTAP).For my tests I am using both FIDO2 Level 1 and Level 2 certified authenticators. One USB device has a button to press to initiate authentication, the other is a fingerprint scanner with some of my fingerprints enrolled. You can learn more about FIDO2 at the FIDO Alliance site or via links on this curated WebAuthn awesome list.
Enabling FIDO2 in IBM Cloud Identity
After signing up for IBM Cloud Identity I contacted the beta administrator to enable FIDO2 support in my instance. I also configured Cloud Identity as SAML-based provider in my App ID instance which I have. The app is based on the mentioned tutorial on end-to-end security. For connecting App ID and Cloud Identity I followed the instructions from the recent blog post. |
| 2FA options in Cloud Identity |
With the foundation in place, I added a new user to Cloud Identity's Cloud Directory, i.e., it's user repository. Because I enabled it, an email with a temporary password was sent to the specified email address. As the new user and utilizing Chrome with an icognito window I logged in to Cloud Identity. There, I first had to change the password and thereafter to confirm my identity with a one-time-passcode (OTP) sent by email. After clicking on my profile, I could add new methods for the second factor authentication (see left).
I picked "FIDO Device" and registered my first device, then repeated it for my second device. It is important to note that only certain browsers with a minimum software level support the registration and authentication flows.
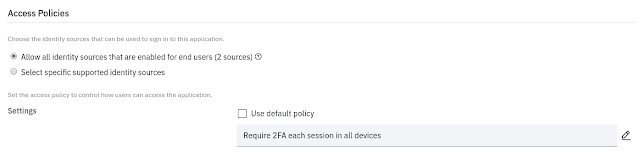 |
| Change from default to 2FA-requiring policy |
FIDO2-based 2FA for IBM Cloud app
 |
| FIDO2 devices for MFA |
With the changed policy in place I logged in to my app again. After accepting my password, the login dialog presented me options for the second factor (see right). Either OTP by email or authenticating by using one of the configured FIDO devices.
After selecting a device I was prompted to insert the USB security key into my computer and to authenticate. This meant either pressing the button on the USB dongle or touching the key with an enrolled finger. Finally, I was logged in and could upload a file to my encrypted cloud storage account (the tutorial app).
If you want to test it yourself I recommend changing the SAML configuration for App ID in Cloud Identity. For the "Name Identifier" change it to "email". It allows the tutorial to work if the user name is not an email address.
In addition to tests described above, I also tried an account without a FIDO2 device. For that case I had configured email-based OTPs as supported second factor. The sent code is valid for 5 minutes.
 |
| Enter One-Time Password (OTP) sent by IBM Cloud Identity |
Conclusions
Enabling the secure web application which is protected by App ID to use FIDO2 devices for the second factor was simple. At this moment App ID's own cloud directory does not support FIDO2, but IBM Cloud Identity does. Cloud Identity can be used as SAML-based identity provider. With the right access policy in place, 2FA is enforced and I could use my hardware security keys for it.If you have feedback, suggestions, or questions about this post, please reach out to me on Twitter (@data_henrik) or LinkedIn.